- What is Cyber Security ?
- Facts about Internet Usage in Africa
- Simba Cyber Security Center
- Simba Managed Security Services
"I don't care if my computer gets hacked, there is nothing on it"
About internet security ?
Your organization's computer systems - and the information they hold - can be compromised in many ways. It may be through malicious or accidental actions, or simply through the failure of software or electronic components. And we need to consider all of these potential risks, it is malicious attack from the Internet that is hitting the headlines and damaging organizations.
The Year 2014 Information Security Breaches Survey1 found that 81% of large companies had reported some form of security breach, costing each organization on average between $600,000 to $2.5m. These findings are supported by almost daily stories of large scale cyber incidents, such as the Gameover ZeuS botnet.
Understanding the capabilities behind these attacks, the vulnerabilities they exploit, and how they are exploited is central to your organization's ability to defend itself against them. Security professionals often focus on the security mechanisms or controls employed without explaining why they are needed, and what they mitigate.
Internet Security - Cyber Defense
In East African scenerio, Specifically Kenya & Tanzania the internet footprint is growing very fast pace as more organizations are offering internet based business and taking advantage of internet reaching their customer base to offer them internet based services. For example, Kenyan BFSI industry has seen a tremendous expansion in terms of internet related services in last 2 years thus becoming vulnerable to intrusions and exploitation. The fast-growing digitally enabled service systems in Kenya is victimized by increasingly sophisticated insiders and outsiders launching more frequent and targeted attacks.
These attackers are using very clever tactics to penetrate inherent weaknesses in basic information security platform and systems, rendering standard methods of detection and incident response is becoming obsolete. Real time threat detection and mitigation is the need of the hour. This is where Simba Technology Limited steps in to provide a platform towards these new requirements.
Hacked Systems can be used for
- Send Spam and Phishing Emails
- Infect and over load other systems
- Harvest and Sell Email Addresses & Password
- Illegally distribute of Software / Music / Movies
- Distribute Pornography
- Become a Malware download site
- Steal Password and used for hacking into other systems
- Steal information from other systems
Internet Penetration in Africa
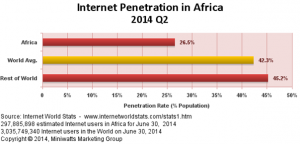
What about East Africa ?

Kenya – Population (2014 Est.) – 45,010,056 Internet Users till 31st December 2000 – 200,000 Active Facebook Users till 31st Dec 2012 – 2,045,900 Active Internet Users till 30th June 2014 - 21,273,738 Internet Penetration till Q4 2014 - 47.3 % Internet % for Africa - 7.1 %
The Kenya National Bureau of Statistics released the 2015 economic survey highlights on May 2015. According to the report the economy expanded by 5.3% in 2014 compared to 5.7% in 2013. One of the sectors of the economy that experienced the biggest growth was the ICT sector that expanded to 13.4% from 12.3% in 2013.
An interesting takeaway from the report was Kenya’s internet penetration which stood at 54.8% of the population or 22.3 million Internet users. Currently around three billion people of the world’s population access the internet which is around 40% of the global population. This means Kenya has by far beaten the global average by far. This growth is attributed to increased affordability of Internet services as provided by ISPs which saw the price of browsing the Internet become more affordable. The growth of E-commerce has also led to increased usage of the internet with Kenyans taking up online shopping. Kenyans have also used the internet for utility services such as online reading of newspapers and online banking services. The government has also heavily invested in e-government services such as online renewal of driving licenses which, have driven the surge in internet usage.
Tanzania – Population (2014 Est.) – 49,639,138 Internet Users till 31st December 2000 – 115,000 Active Facebook Users till 31st Dec 2012 – 705,460 Active Internet Users till 30th June 2014 – 7,590,794 Internet Penetration till Q4 2014 - 15.3 % Internet % for Africa – 2.5 %

Uganda – Population (2014 Est.) – 35,918,915 Internet Users till 31st December 2000 – 40,000 Active Facebook Users till 31st Dec 2012 – 562,240 Active Internet Users till 30th June 2014 – 6,523,949 Internet Penetration till Q4 2014 – 18.2 % Internet % for Africa – 2.2 %

Sudan – Population (2014 Est.) – 35,482,233 Internet Users till 31st December 2000 – 30,000 Active Facebook Users till 31st Dec 2012 – N/A Active Internet Users till 30th June 2014 – 9,307,189 Internet Penetration till Q4 2014 – 26.2 % Internet % for Africa – 3.1 %
SIMBA CYBER SECURITY CENTER (SC²)
The Simba Technology’s Cyber Security Centre (SC²) monitors the activities and events in the client’s IT environments to ensure that anomalous traffic and activities are detected, identified, classified depending upon used cases with reference to the rules & policies defined and actioned upon each of these identified anomalous activities. Simba Cyber Security Center (SC²) engagements are managed along with the active involvement of customer’s IT Team where ever actionable are recommended in the event of identified threat or malicious activity. Simba Cyber Security Center (SC²) engage in reviewing of all activity and create reports to provide technical security overview with meaningful data versus non-threatening anomalies. Customer control environment procedures are also monitored to ensure that breaches of these procedures and the possible precursors of malicious activity are identified and reported.
Simba Cyber Security Center (SC²) engagements
The Simba Cyber Security Center (SC²)’s main focus is to provide security and compliance. Cyber Security monitoring at SC² guards client’s critical IT Infrastructure analyzing the events happening with relation to the infrastructure and co-relating these events with automated event co-relation engine, any indication of malicious activity or event is automatically detected with in few seconds and SC² team get alerted with in few seconds of the anomalies detection. Entire process is automatic no manual intervention, which is less expose to human errors in detecting an attack or event of security breach. SC² team will alert clients immediately of a potential security breach being detected that could compromise the integrity of client’s network and can assist with remediation. It’s a cost-effective, peace-of-mind solution to safeguard your network and your business critical data.
Daily and monthly analysis and reports provide the enough evidence required to take action against threatening anomalies that are detected and can be acted on time, while managing ISO / SOX / PCI compliance demands of all events recording and identification.
In the event of Security breach, SC² provides actionable counter measure the event. SC² will also provide forensics report where ever applicable and appropriate, and will help maintain the proper evidence for legal action.
Simba Cyber Security Center (SC²) offerings
Our Enterprise Security Services perform comprehensive testing and audits and provide the security solutions to protect your business-critical systems including:
The services offered by the SC² allow to identify, plan appropriate answers and react to cyber threats, ie, SC² offers the following services,
- Event monitoring with automatic event co-relation with co-relation engine and signatures.
- Incidents detection and management
- Maintenance of systems in secure conditions
- Cyber Intelligence, threat and vulnerability monitoring, assessment and mitigation
- An security audit and analysis of the compromised network and a posterior analysis of the extent of attacks
- Audits and tests (technical infrastructure)
- Crisis management assistance
- Security and footprints indicators
Simba Cyber Security Center (SC�) differentiator
Operational Differentiator
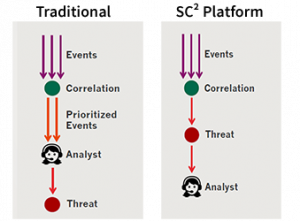
Correlation focused on identifying threats against prioritized events,
- Pre-identified threats that are evaluated for false positives provide better accuracy
- Manpower required for analysis is minimal and non- skilled
- Threat are detected in real-time
- Consistency in detecting threats impossible for manual processes
Simba Managed Security Services
Comprehensive Network Attack Management (CNAM)
- Leverages a custom developed correlation engine
- Analyses event data from firewalls, NIDS/IPS,HIDS/HIPS,OS, Databases
- Recommends action to deal with the attack
APT (Automated Penetration Testing) & VA (Vulnerability Analysis)
- Artificial intelligence based technology that emulates the hacker
- Eliminates vulnerabilities missed out by scanners and manual PT/VA















